WHY CIS FOR
CYBER SECURITY?
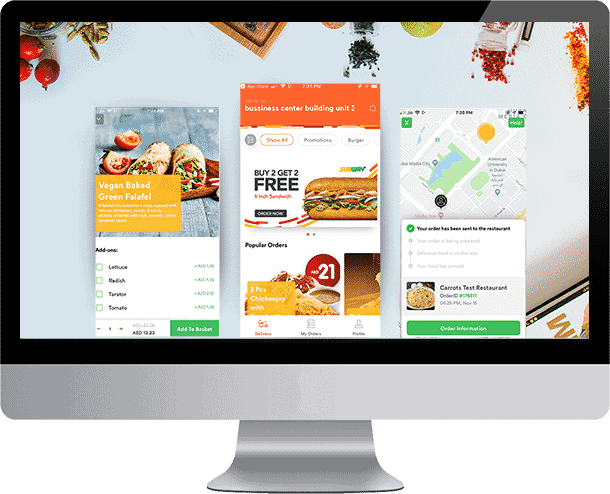
CIS is a cyber security services provider company that expertise in a range of investigative and defendant security solutions. We are ethical hackers team that has know-how and futuristic technology background and knowledge to provide your business internal internet based operations with un-hackable security.
Modern cyber threats are thus fought on unbending technology solutions helping you have a care-free corporate business life. Design expertise, optimal security solutions allow us to provide you Cyber Security as a Services to secure your operations. Our cyber security solutions include cyber security advisory, realistic hacking simulation, organizational training, in-depth investigations, cyber security evaluation.
Our core competence is in domains of healthcare, telecommunication, financial services, industry manufacturing etc.
42
Team members
174
Hacking Simulations
386
Cyber Projects
112
Closed IR cases
We lead in

Smart Security Operations Center
Go a step ahead of your current security potential and live in the enriched and modern security solutions. Experience the true -smart at our security operations center. Easy to adapt and monitor, actively responding to cyber incidents, gathering and analysing intelligent system on important security aspects and so on.
Cyber Security Evaluation
We are CIS sensitively works to identify any flaws and loopholes in your cyber defences of your organizations. By evaluating potential threats, we are able to lay strong solutions on possible attacks while strengthening your security from within.


Realistic Hacking Simulation
Confidential information and sensitive data are protected at all costs. We provide you pragmatic IT solutions for protecting your confidential information. Ethical hacking is used to secure your organization process, data and internal information form cyber world threats.
Employee Training
IT Security Solutions are used and placed in integral parts for enforcing and maintaining superior cyber security mechanism for any organization. It becomes important to educate and train your staff to contribute and support security endlessly in that process.

Our Industrial Core Competence
We use a set of testing to gain statistics to fuel our cyber security solutions. With analytics driven approach you are able to get best solutions and security patches.
White Box Testing
- Security Level: Average
- Full Knowledge Required
- Testing As: Developer
Black Box Testing
- Black Box Testing
- Zero Knowledge Required
- Testing As: Attacker
Grey Box Testing
- Security Level: Intermediate
- Some Knowledge Required
- Testing As: User
Benefits of Testing
- Detection of Breaches
- Data Vulnerability Checking
- Effective Patching
Our Cyber Security Services that we offer
Regression audit
Close security speculations of your website.
Remediate
Fixtures in code deficiencies.
Reports
Give you a complete information on the important changes.
High Level Security
We provide you ultimate cyber security solutions
Scan & Detect
Detection of security breaches and fix them.
Exploit
Prevention from data exploitation
Cyber Crime Consultancy
Continuous connection for securing data.
POC with the Instructions
Feasibility is rendered.
Manual Testing
Cyber Security as a Service with quality
Vulnerability Patching Support
Decrease the vulnerability security is achieved.
Priority Based Auditing
Share with us your needs, vision, priorities
Annual Security Reports
Transparency in process, annual reports are shared.
Our Industrial Core Competence

Healthcare
Data security and secrecy are the one of the major needs of the Healthcare sector. We at CIS thus always keep you one step ahead of these global regulations by providing you a well-integrated and secure internal software system protecting your patient private data and internal working.

Our Service-based Organizations
We approach your needs by consulting you about your very needs. Here you can leverage innovative IT solutions to get deeper understanding of the current processes, use of technology and to improve your security. Thus, with IT Solutions you are able to get through the complex needs.

Industry Systems
Use of cyber security as service allow you to take control of your system and physical assets, management of automated operations and security, industrial operations and other security and protection needs. Industrial cyber security solutions, especially new-age industries needs and requirements.

Telecommunication
Knowing your requirements being a bit more than the other industries, we try to keep your extensive data secure during the management, storage and communications, share and much more. We provide you the cyber security that matches your robust infrastructure needs. Tailor made solutions are provided.

Fintech
Going digital and providing banking and finance services online require a lot of measures and layered data and process security needs. We provide you digital channels for the sake of users and your internal process to keep transactions always secure and cyberattack proof.